According to CNN's recent report, an attacker in South Houston received control of the human-machine interface (HMI) of the SCADA system that controls part of the water treatment plant. In this case, HMI security uses only a password that is easily guessed. Security has now become the top priority for embedded developers because the systems they create can and will likely be used for important infrastructures that are becoming more automated and often connected Working, in some cases, may also be connected to the outside world. Certain types of equipment already have certain security, because starting from the initial concept of these equipment is the first requirement of security, such as communications equipment used by the government and troops. However, most devices are potentially insecure. It is important to realize that no device is absolutely secure, and developers need to work hard to improve security through good design, programming and configuration. Best safety measures There are many basic rules and principles in the industry that can be used to guide design and development decisions during product development (Table 1 below). The first and most important is to realize that security needs to be embedded inside rather than outside. It is important to improve existing and traditional systems as much as possible, and new projects should consider security from the very beginning, and doing so will pay off well in the follow-up process of the project. The following is a list of the best security measures applied to embedded development: (Source: Security Code by Michael Howard and David LeBlanc, 2004) It is worth noting that no system is absolutely safe. However, as we will see later, following some practical methods can greatly improve the security of embedded systems. In some cases, these technologies can be applied to existing systems; in other cases, they can become recommendations for future system designs. Apply best practices to your embedded system (1) To achieve a more secure configuration. Although embedded security has been well-publicized, many operating platforms based on these systems can achieve higher security through proper configuration. Security flaws are likely to have been fixed in the new operating system, and there may still be loopholes in the old version. The default configuration of the embedded operating system is usually adjusted for performance and memory capacity, and many functions are turned off by default. Follow the manufacturer's guide to activate security features, including: By selecting a more secure configuration, many attack vectors for targeting devices can be removed. It is best to assume that the device will be attacked at any time, and to ensure that the configuration received by the user itself is more secure. (2) Secure network communications. Many of the security problems of existing embedded systems stem from networks and access that are open to the public (enterprise networks) and even directly to the Internet. The more conservative view is that all external connections to the device are insecure. The continued popularity of devices in the user community will create use cases that you cannot imagine. The best way is to protect all communications to and from the device. (3) Divide the system for protection. Dividing the different major components of the system into multiple parts is an effective security technology. In many cases, these partitions are physical. Virtualization can also be used today to achieve virtualization segmentation, that is, segmentation by software on the same device or processor. An example here is to integrate Microsoft's general operating system (GPOS) such as Windows or Linux with a real-time operating system (RTOS) on the same device, but each system runs in its own virtual environment. In this way, the security attacks and vulnerabilities occurring on GPOS will not affect the mission-critical control functions performed in the RTOS. Similarly, GUIs and remote access to devices can be grouped together to separate control systems. In this way, a remote attack that denies service or destroys the GUI part will not affect the control system. The advantages of this system combination are very significant because it can greatly reduce hardware complexity and cost. With virtualization technology and the latest multi-core processors, this combination is now very practical and cost-effective. In addition, the separation of critical and non-critical tasks facilitates the improvement of the safety and insurance factor of these devices. Figure 1 below shows an example of an embedded system divided into multiple modules. An attacker may be able to access or destroy GPOS, but it cannot affect other parts of the system. The virtualization layer can ensure that processor time and access to hardware resources are properly shared, thereby preventing damaged parts from affecting other parts. For example, if GPOS is destroyed or enters an endless loop, it will not stop the critical parts of the system. In fact, the normal operation of the system can be restored by restarting the GPOS section. Reinforcement system resists attack Activating the security features of the embedded operating system is the first step, but it is important to continuously test the system throughout the development process. It's also reasonable to use automated tools to test field products, if possible, so that you can see what weaknesses exist in the product line. Such tests can identify vulnerabilities in the system and can then be fed back to the development process through bug fixes and configuration tweaks. Third-party testing and certification may be considered based on market conditions suitable for the equipment. In the area of ​​industrial control, Wurldtech Achilles certification ensures that the device passes a rigorous security test. Using these tests during development can continuously harden the equipment. Comprehensive and diverse security testing is the key to improving embedded security. Protection startup and execution process Embedded systems are very vulnerable to attacks during startup. In fact, it is common to see amateurs reflash consumer hardware flash, but for systems that are part of an important infrastructure, this is not a due obligation. Many devices allow upgrades through network interfaces or other remote access methods, which can pose serious security threats if abused. Protecting the boot image is an important step in protecting the device. A trusted boot image can be cryptographically signed with an identifier, which should be considered by the hardware as the only acceptable signature. The support of processor hardware makes this method very popular. A trusted execution method can always ensure that only properly signed applications/libraries/drivers can run on the device. This will prevent malware from being installed on the device. Protect data and data storage No assumptions should be made regarding the classification and privacy of data used in embedded systems. Traditionally, device data is not considered private or third parties are interested. However, the role of embedded systems in health care, energy systems, power grids, water treatment and wastewater control applications is increasing. External threats may be interested in the data carried by these devices. Therefore, data should not be stored in clear text, and encryption techniques should be used whenever possible, especially when data is stored on disk or flash memory. In particular, do not store passwords and keys in clear text (this is obvious, but this situation still occurs). Now, the embedded processor has hardware acceleration for the supported encryption algorithms. Therefore, it is entirely possible for embedded devices to implement complex encryption algorithms without significantly burdening the CPU. Mapping suggestions to best practices These suggestions can be mapped back to the best security measures. It is worth noting that the suggestions in Table 1 may only partially satisfy the intent of the best method and cannot fully meet their requirements. The best method should be interpreted as continuous goal design and development rather than a checklist. Improve security at the embedded operating system level The awareness of security should be stronger and stronger for embedded developers. This is indeed the case. Security needs to be implanted, and it is always implemented from the initial concept to the final release. However, some reasonable measures can be taken now and in future projects to improve the security of the embedded operating system. Following some excellent security measures, such as using security defaults, stopping unimportant services, and protecting data, can significantly increase the security of embedded systems. No system is absolutely safe, but it can be ensured by continuous improvement to achieve a better state. Digital currency transactions allow users to convert existing digital currencies into other digital currencies. The entire transaction does not involve any legal tender. Because of the relatively loose regulation, the mainstream digital currency trading platform also opened this function.Digital Asset Exchange (DAE) is a platform for matching transactions between digital currencies, digital currencies and legal currencies. It is the main place for encrypting the circulation and price determination of digital currency transactions. Currency Exchange,Digital Currency Exchange,Virtual Digital Currency Exchange,Display Currency Exchange China youbi digital assets limited , https://www.ubcoinchina.com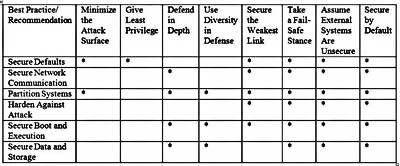
Table 1: Relationship between safety recommendations and best practices.
Minimum privilege: Assign an application, task, or process just enough permissions to complete the current job. Too high permissions can cause unnecessary access or behavior.
Defense in depth: Use more than one protective layer and don't expect one layer of protection to provide complete protection.
Diversity Defense: Use different types of protective equipment, software, or vendors.
Protect the weakest link: Protect the most insecure components, interfaces, or applications. This is where you are most likely to be attacked. Because the security level of any system can only be based on the weakest component (barrel theory).
Error protection status: Expect to find vulnerable points; be ready to accept physical and remote attacks on the system.
Assumptions about external systems: Do not expect other devices connected to your product. You can't assume that the external device is secure, and understand that your device may be connected to a completely open network.
Default Security: Set the system's default configuration and behavior to be as secure as possible. Turn off features, services, and access that are not necessary for most users.
Simplicity and Usability: Use simpler designs that have potentially fewer security holes and vulnerabilities and are easier to understand, examine, and test.
Activate the network firewall. A modern real-time operating system (RTOS) has a network firewall function, and any device with a network connection should have a firewall enabled while it is running.
Disable all unimportant services. Only activate services that are essential to the operation of the device.
Activate or include powerful cryptographic libraries when needed.
Memory protection is activated through the memory management unit (MMU); real-time processes (RTP) are used instead of kernel levels.
Unless absolutely necessary, it should be performed with user rights.
Activate the network firewall; only allow communication over the specified TCP/IP port.
Activate secure communication channels: IPsec, SSH, SSL, or VPN access.
Suppress unsecured services such as Telnet.
Disable debugging service if possible. If it cannot be prohibited, make sure these services are safe.
Device-to-equipment and device-to-control communications should consider using a VPN-based infrastructure as much as possible. 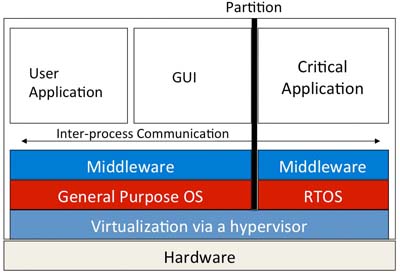
Figure 1: System partitioning for security.
Compared with traditional stock exchanges, digital asset trading platform not only matches transactions, but also plays the role of market maker and investment bank. The role of the market maker in the trading platform can increase the liquidity of the market, and the trading platform can earn the transaction price difference. The role of the investment bank of the trading platform is to provide services such as issuance and underwriting of digital currency, from which the trading platform collects money fees, or collects deposits in the form of community voting of the trading platform.
The best way to improve the security of embedded operating systems
In the past year, security has quickly risen to the most important position for embedded developers. Although the Stuxnet worm awakens the security awareness of the embedded industry, there have been many other noteworthy events since then. For example, as reported in the CBS News, the attacker can gain control of the home insulin pump and change its setting parameters, which may seriously endanger the patient's personal safety.